As a software product owner or an architect, you may have found yourself caught in a situation where you need to migrate your legacy system to a modern system, but unfortunately, the migration can be lengthy and time-consuming. So you may have been tasked to carry out the migration gradually over a period of time, thus ensuring that the new application should be able to utilise the legacy resources such as data.
More often than not, your legacy system may have issues due to which it is not able to perform well to cater to your present needs. For instance, your legacy system database is too complex with very tight relationships that need to be broken down to support your modern cloud architecture pattern. Maybe the legacy APIs are obsolete and your modern system requires new APIs and frameworks.
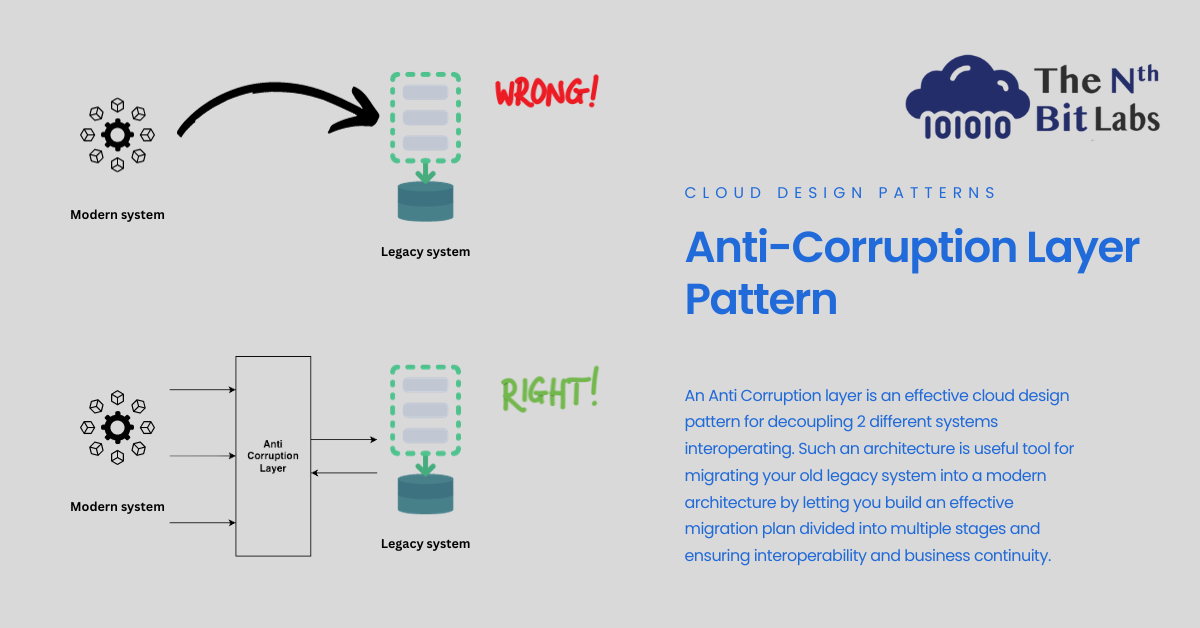
To support the smooth transitioning from the legacy system to the modern system, your systems need to interoperate. Hence, maintaining access between new and legacy systems can force the new system to adhere to at least some of the legacy system’s APIs or other semantics. So the problem is the potential corruption of your modern clean architecture in order to support the legacy system/features. A similar problem arises when dealing with external 3rd party systems.
The solution I am about to explain is called the Anti-Corruption Layer Pattern. But before I move forward and talk about it in detail, I want to establish the fact that this solution needs to be considered in the following scenarios:
- A migration is planned to happen over multiple stages, but integration between new and legacy systems needs to be maintained.
- Two or more subsystems have different semantics but still need to communicate.
Also, note that this pattern may not be suitable if there are no significant semantic differences between new and legacy systems.
Solution
The solution is building an adapter layer or an anti-corruption layer between the two systems. In essence, this layer translates communication between your legacy system and your modern system acting as a gateway. This allows legacy systems to be unchanged and yet at the same time makes sure that your modern system design stays uncompromised.
A good scenario could be thought out to be as your legacy system is a monolithic architecture that was designed some years ago to support the business requirements back then. But your modern architecture and AWS design pattern is a service-oriented architecture and supports different applications. Some services need access to legacy functions during the migration stages for interoperability and business continuity.
Now that you’re aware of the significance of data security in safeguarding your business against potential data breaches, let’s delve into what data security entails and how it can be beneficial for you.
The design for such an anti-corruption layer is simple but may add a certain level of complexity per use case basis. Some of the design considerations when architecting such an anti-corruption design pattern could be:
- Consider the scalability of your anti-corruption service.
- Consider the latency introduced due to additional calls required.
- Consider the additional effort required to maintain and manage.
- Consider if your anti-corruption layer requires more than 1 partition.
- Consider when you will retire the anti-corruption layer since it is part of your migration strategy.
Similarly, there could be more design considerations and factors that you may need to consider if you are planning to retire your legacy system to a more advanced modern system and are not sure about how to go about it.
Are you facing the challenge of migrating your legacy software to a modern architecture? Don’t let the migration process overwhelm you. Trust The Nth Bit Labs for a smooth and successful transition. Our Anti-Corruption Layer Pattern expertise ensures your legacy systems remain intact. Take the first step towards modernizing your software with confidence.